For years secure areas have been protected with pin pads or fingerprint biometrics in conjunction with an access card. Unfortunately, neither pin pads nor fingerprint biometrics provide a secure, ubiquitous solution. Pin codes could be shared and readers containing a fingerprint sensor haven’t worked for all people in all conditions.
Advances in technology have provided companies with new options to ensure the security of their premises. To solve the problems of the past both facial and iris biometrics are increasingly deployed. These biometric authentication solutions work by using individuals’ unique biological features to verify that individuals are who they claim to be. They are both ubiquitous, can’t be shared, and have been proven to be reliable and secure.
However, contrary to popular belief, these biometric authentication technologies are not the same. So which biometric methodology is the best option to secure your building, and how do they compare to each other?
Here’s a rundown on everything you need to know about today’s biometric authentication technology, including whether to choose facial or iris biometrics for your business security needs.
The Future of Physical Access Control with Biometric Authentication
It’s best to review the future state after a common understanding of the past and present. A Physical Access Control System (PACS) is a security system designed to restrict or allow entry to specific buildings or areas. Access Control systems replaced the lock and key over 20 years ago and are deployed in every modern enterprise across the globe.
Unlike strategic landscaping, fences, or retaining walls, PACS can regulate who gains access to a certain part of your property or facility, as well as when and how they access the area. Coupled with biometric authentication, the data is irrefutable as each authentication is tied to the physical attributes of a single individual. This is precisely why companies need modernized systems as they can help to deter unauthorized attempts which may lead to trespassing, theft, vandalism, and carelessness by authorized employees which allow for others to tailgate, cross or piggyback into a building by following an authorized entry.
History of Physical Access Control
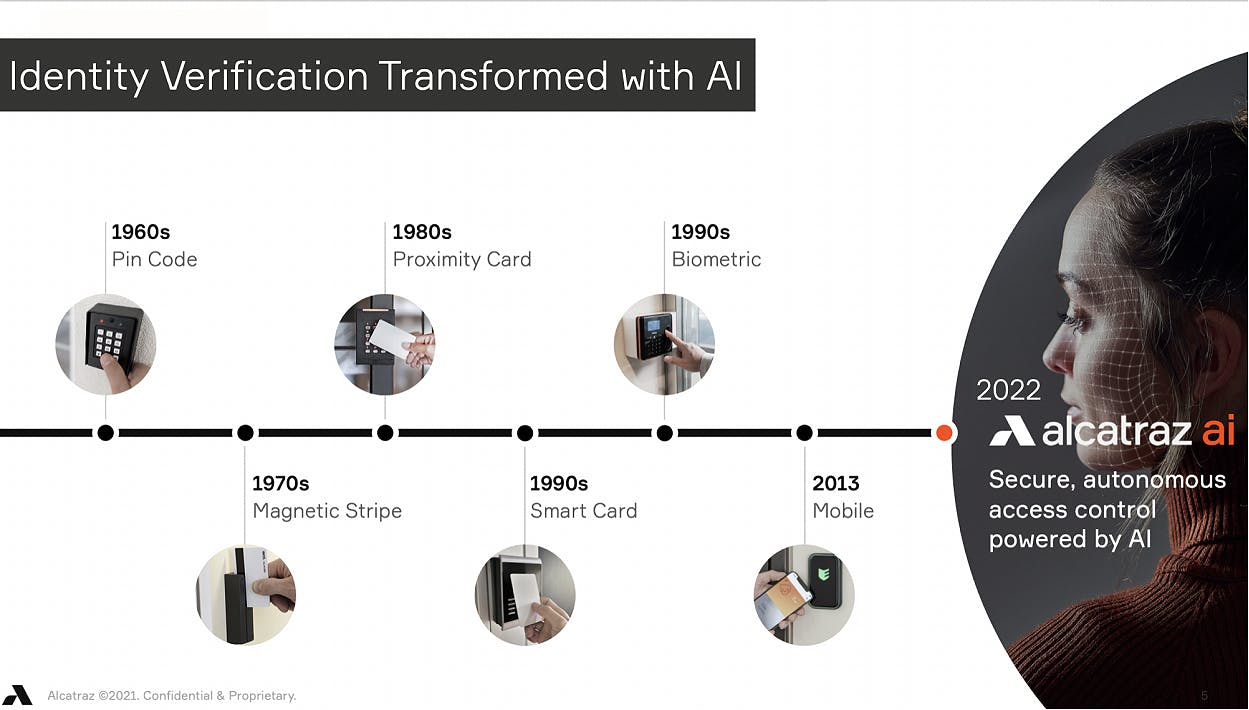
Radio-frequency identification (RFID) badge readers and key cards are used in the majority of corporate buildings today. RFID cards, commonly known as Prox Cards, replaced the metal key in (Date) as they could be deployed to many people, they were easy to use, and most importantly could be centrally managed and revoked when access was no longer required. While there have been a few advancements in the security of these cards, many buildings continue to utilize an insecure card technology that is relatively easy to clone.
Today’s security can be circumvented easily even if a multitude of security personnel are deployed, as it is impossible to watch every door at every moment - even with the assistance of the best camera security platforms. Guards are expensive and can be distracted. There are better options available.
Most modern companies adopt access control solutions to safeguard their people and their assets. Highly secure areas use biometric authentication and multiple factors. Unfortunately, traditional biometrics do not provide the speed or convenience required to secure all areas.
Essential Components of Access Control in Today’s World
When it comes to biometric authentication for access control, the solution you choose should feature several core components.
Look for a solution that provides a frictionless, no-touch experience. This helps to secure assets, data, and employees while simultaneously providing for an uninterrupted flow as users enter secure areas. Today, this has become even more relevant as most businesses attempt to reduce the spread of germs.
Make sure you prevent one of the most common vulnerabilities, unauthorized access. Tailgating is a problem that has been mostly ignored, aside from using cameras and security guards, yet it should be a must-have component in any holistic security system. Tailgating occurs when an authorized user unwittingly allows an unauthorized user to sneak in through an open door after he or she has gained access. Most anti-tailgating products today are ineffective, very expensive and difficult to install. However, a real-time biometric authentication solution like the Alcatraz AI Rock detects this type of breach by identifying individuals as they attempt to access restricted entrances.
For highly secure areas, choose a solution that offers multi-factor authentication.
Two-factor or three-factor authentication can be used in tandem with a badge reader
to add another layer of security.
How does the Alcatraz Rock prevent tailgating? The Rock uses the latest advancements in computer vision technology to verify authorized individuals in real-time and to determine whether a single or multiple people entered a secure area at the time of authentication.
If unauthorized users follow authenticated users through doors, the Rock will identify
them as tailgaters, and alerts will be issued to the existing access control system.
Additional Features of Access Control
To effectively secure your premises with biometric authentication, it’s imperative to understand that not all biometrics systems are created equally. A few components that set products apart are as follows:
Power of Artificial Intelligence (AI)
Artificial Intelligence (AI) is changing the face of access control. As an example, the latest video management systems have the ability to use AI to recognize foreign objects and offer analytics to review access patterns to detect anomalies to prevent a security incident.
As part of a biometric authentication solution, AI can provide an adaptive capability to detect various lighting conditions and adjust accordingly. AI can also be used to detect whether or not a person is wearing a mask, or other required protective wear, before providing access. The Alcatraz Rock utilizes AI and advanced deep learning algorithms to detect small changes from an enrolled individual’s profile (is the user wearing glasses or a hat; did they grow or shave a beard; has their hairstyle changed). Since the enrolled data is continually appended with new information, the Rock can provide the best user experience and high level of assurance required for access. Technology that can adapt to real-world, changing conditions is a must-have in any zero-trust business environment and provides any business looking to secure a space with the peace of mind that the right users are getting in, while those that are unauthorized remain out.
ID Verification
ID fraud, when one user shares another’s ID credentials, is difficult to detect without biometric authentication. However, if one’s biometric information is used as part of the authentication process, each and every time a person gains access, an irrefutable record linked to the badge number associated with the enrolled individual is created.
Passive Credentialing
Another important component of any modern physical access control system is to ensure that the system is non-intrusive. Security systems that are easy to use tend not to be circumvented by valid users. Those that remove a need to enter a pin code, or carry another device containing a credential are more readily accepted by users. With the Rock, your face is your credential, and opening a door is as simple as, well, opening a door. There is nothing else to carry and nothing else to remember. Just you and your face. Removing user friction allows for seamless throughput in environments that utilize turnstiles, elevators, executive areas, and even the cafeteria. Before deploying any biometric authentication system it is important to think of your end-users and the impact the solution will have on their ability to seamlessly access areas where they are authorized.
Effortless Assembly
The ideal biometric authentication solution should be easy to assemble and implement.
For instance, look for technologies that can simply plug into your existing control environment.
As an example, the Alcatraz AI Rock connects to any existing access control systems using power over ethernet and can send badge information and events via Wiegand or OSDP.
In most implementations, the Rock can be installed and operational in less than 1 hr.
Simple Integration
Most buildings today have an existing access control solution. When considering a biometric authentication solution, it is important that you determine how the solution fits into your current environment. Does the biometric authentication solution work with your current access control system? Is there additional integration required for it to be functional, or fully featured?
Is there a cost for this integration? Upon installation, what is required for each reader?
Does the biometric authentication solution provide a video stream that can be viewed in your existing access control or video management system? The Alcatraz AI Rock requires a single POE+ connection and directly connects to an existing card reader and access control system. When an event occurs (authentication or otherwise) the back-end access control system receives a card number via Wiegand or OSDP, just as if the card were present.
Additionally, a video stream can be via an ONVIV standard with a clip of the event - either allowing Security to take action immediately or making a forensic exercise much easier
after the fact.
Architecture Options
Biometric authentication solutions should have the capability to be deployed how you want and according to your security policies. Deploy and manage as a complete On-Prem solution; or deploy a cloud-based solution that shifts the expense from the Capital budget to the Operations budget via a subscription model. As a customer, you should choose what is right for you.
Biometrics: A Key Component in Modern Access Control
Of the multiple features included in a modern access control system using biometric authentication, the biometrics component deserves the most focus, as it will determine whether the solution is used or not. . Facial biometrics uses the unique characteristics of the human face as the core credential for private and autonomous access. Using the characteristics of a face is far more effective than using a fingerprint, for example, because facial authentication tends to provide greater reliability. Dirty fingers, wet fingers, and even dry fingers can make it difficult for some to authenticate themselves. Biometric authentication modalities using the finger or the hand, such as fingerprint, palm-vein, or hand geometry require user interaction. In some instances, placing a hand on a sensor is not convenient, especially if one’s hands are full. There are better options.
Biometric Authentication Works for All Industries
Biometric authentication provides a high level of security and user convenience which is applicable in a myriad of applications in multiple industries. For high throughput in a corporate lobby, biometrics can be used as a replacement for a badge as a single factor. For higher security use cases such as data center access or access to critical infrastructure, biometrics
can be paired with a third-party badge reader for two-factor or three-factor authentication. Depending on your environment, biometric authentication can provide the right level
of security with the least amount of friction.
For instance, banks use biometric authentication to decrease access to their high-risk areas. Likewise, healthcare organizations keep their staff and patients safe by reducing touchpoints while also making sure that only authorized personnel can access secure areas.

Iris Biometrics vs. Facial Biometrics
Now that we’ve explored biometric authentication in general, let’s take a closer look at the technologies of facial and iris biometrics to determine which one is superior.
Iris Recognition
Iris recognition uses infrared light and a digital camera to capture a high-contrast image of the iris. However, iris scanner hardware is expensive, user training is required and the size of the systems is typically large. For high-security areas, iris scanners may be appropriate as they are highly accurate, however for areas that are used regularly, iris scanners may not provide the best user experience.
Iris matching algorithms scale effectively, are relatively fast once an image has been acquired. These factors make iris biometrics an effective biometric authentication option in areas where the best user experience can be sacrificed for a high level of assurance.
Pros
- Accurate in Ideal Conditions
- User Consent is Implied
Cons
- High Learning Curve
- Requires Attended Enrollment
- Does Not Work for All Users
- Does Not Respond in All Conditions
- Relatively Slow to Authenticate
Facial Biometrics
As an alternative to iris biometrics, facial authentication stands out as the most convenient and secure biometric authentication technology.
Facial authentication is the most non-intrusive form of biometric authentication. It is important to note, however, that each facial biometric solution uses its own method to adjust for various lighting conditions - and some are better than others. Additionally, some solutions provide a large screen that provides user feedback to ensure the face is aligned correctly. Others, such
as the Rock do not require a large screen as they use multiple sensors and AI to detect a body, locate the face, determine liveness and authenticate the user - all in a fraction of a second.
Quality facial authentication products can provide additional features as mentioned earlier in addition to acting purely as an authentication device.
Other reasons to use facial authentication include the following:
- 1-N matching
- Reduced costs
- Seamless implementation with existing access control system
- Two-factor and three-factor authentication
- Touchless access
Pros
- Hygienic - No User Interaction or Contact
- Fast
- Authenticates Unique Credentials
- Quality Video at Eye Level
- Computer Vision and AI Provide Unparalleled Capabilities
- Irrefutable Audit Trail
- Enables a Frictionless and Passive Experience
Cons
- Some systems are sensitive to lighting conditions
The above-listed benefits make facial authentication a top choice for data centers, where you can use this technology for visitor authentication and access. In addition, it can be used in the financial sector for regulating employee building and vault access.
Secure health care environments and pharmacies may also want to tap into this technology’s potential to control access. Likewise, governments may rely on this technology to manage building access and promote access. Finally, sports arenas and stadiums may use it to control who enters practice facilities or even VIP lounges.
Your Face is Your Credential
Facial biometrics is by far the best solution for biometric authentication and will continue to replace iris biometrics, finger and hand-based modalities - not to mention security guards, RFID cards, and pin-pads. Facial authentication uses the human face, which is inherently unique, as the key credential. With additional capabilities provided through the use of AI and deep learning such as the ability to detect tailgating, crossing, piggybacking and link high-quality, eye-level video stream of the event to the applicable Access Control or Video Management System, advanced facial authentication solutions provide the combination of security and convenience as never before.
Choose Alcatraz AI: Your Source for Private and Impenetrable Access Control
Designed in the United States, Alcatraz AI has developed the future of access control technology providing a simple and secure experience for those that install, manage and use the technology to access secure spaces. Alcatraz AI provides autonomous access using your face as your credential.
Whether you are a facilities director that is working on safer ways to protect your employees as they return to the office or a better way to secure areas that require multiple factors before providing access, Alcatraz AI can help.
Start a 30-day Rock trial today!
← Previous -- Next →
Tag(s):
Blog
Other posts you might be interested in
View All Posts
Blog
3 min read
| August 19, 2025
Modern Biometrics Can Actually Enhance Your Privacy
Read More
Blog
13 min read
| July 31, 2025
Bring Biometrics to Your Existing Access Control Infrastructure Without Sacrificing Privacy or Flexibility
Read More
Blog
4 min read
| August 8, 2023
Quantifying Benefits: How Facial Biometrics Deliver ROI in Security
Read MoreSubscribe to email updates
Additional content around the benefits of subscribing to this blog feed.


