Rock solid facial authentication for data centers
Effective data center security starts at the perimeter. The Rock from Alcatraz provides a physical security layer as strong as your firewall—powered by facial authentication, AI-driven tailgating detection, and real-time analytics. When security is your brand promise, Alcatraz ensures it’s never compromised.

Flexible enrollment
Enroll in-person or from the comfort of home with transparent opt-in consent.

Effortless access
Enrolled users instantly authenticate with just their face, eliminating the need for physical credentials or mobile devices.

Privacy at the core
Rock X features privacy-by-design architecture, transparent opt-in consent, and robust data protection measures.

Rock-solid security
Offering AI powered facial authentication, intelligent tailgating detection, video at the door and SIP intercom in one device.

Works in all conditions
Rock X boasts an IK08 impact-rated design, operates in all lighting conditions from 0 to 120k lux, an IP66 rating for dust and water protection, and can function in extreme temperatures from -40°F to 150°F.

Connects to your ACS
Add Alcatraz to your existing ACS without custom integration. Simply install the Rock X in line between any Wiegand or OSDP and the ACS. Deploy in the cloud or on-prem.
Ready for
multi-factor authentication

Secure every critical access point, in all locations
Protecting the perimeter of your data center is the first line of defense against unauthorized access. Alcatraz delivers enterprise-grade scalability and high availability, ensuring continuous security across all access points.
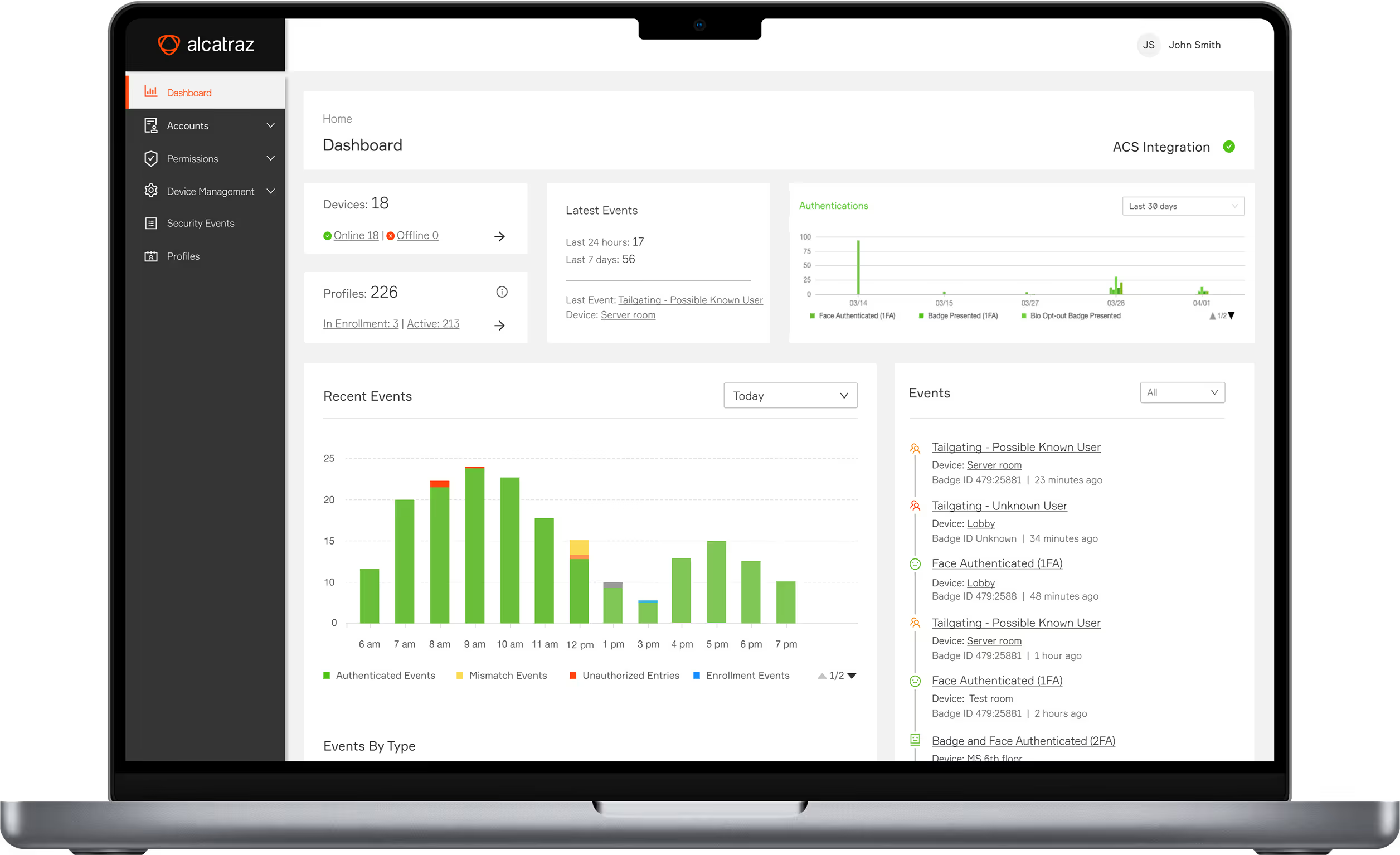
Centralized access control management
Building perimeter
Corridors and hallways
Computer rooms
Server racks
Remote access points
Employees protected by Alcatraz
Of the top 10 AI leaders trust Alcatraz
Customer satisfaction rating
Discover the power of Rock X
Easy integration and deployment
Rock X installs easily between any Wiegand or OSDP reader and the ACS, enabling fast, plug-and-play setup in both cloud and on-premise environments—even in harsh conditions.

Enhanced compliance and data protection
Reduce costs by eliminating physical credentials and admin tasks. Rock X’s rugged build, auto-enrollment, and updates ensure reliability and operational savings.

Reduced operational costs
Rock X protects privacy with encrypted, anonymized data and a one-way biometric algorithm linked to badge IDs—ensuring compliance with GDPR, CCPA, and BIPA.







